
-
Transcripted Summary
Turning your attention now to the Inspec Command Line Interface, we take a look at the two most important commands, exec and shell.
The exec command runs all controls and profiles against your target.
The target is the system you want to scan for compliance.
Due to client-server architecture, you can audit remote systems from a centralized workstation.
The target could be an operating system or API on which InSpec performs the audit.
The API target can be a cloud provider like Amazon Web Services, Azure Cloud, or Google Cloud.
With the exec command you can execute InSpec commands on localhost or other targets or remote via SSH or via WinRM, or via Docker connections.
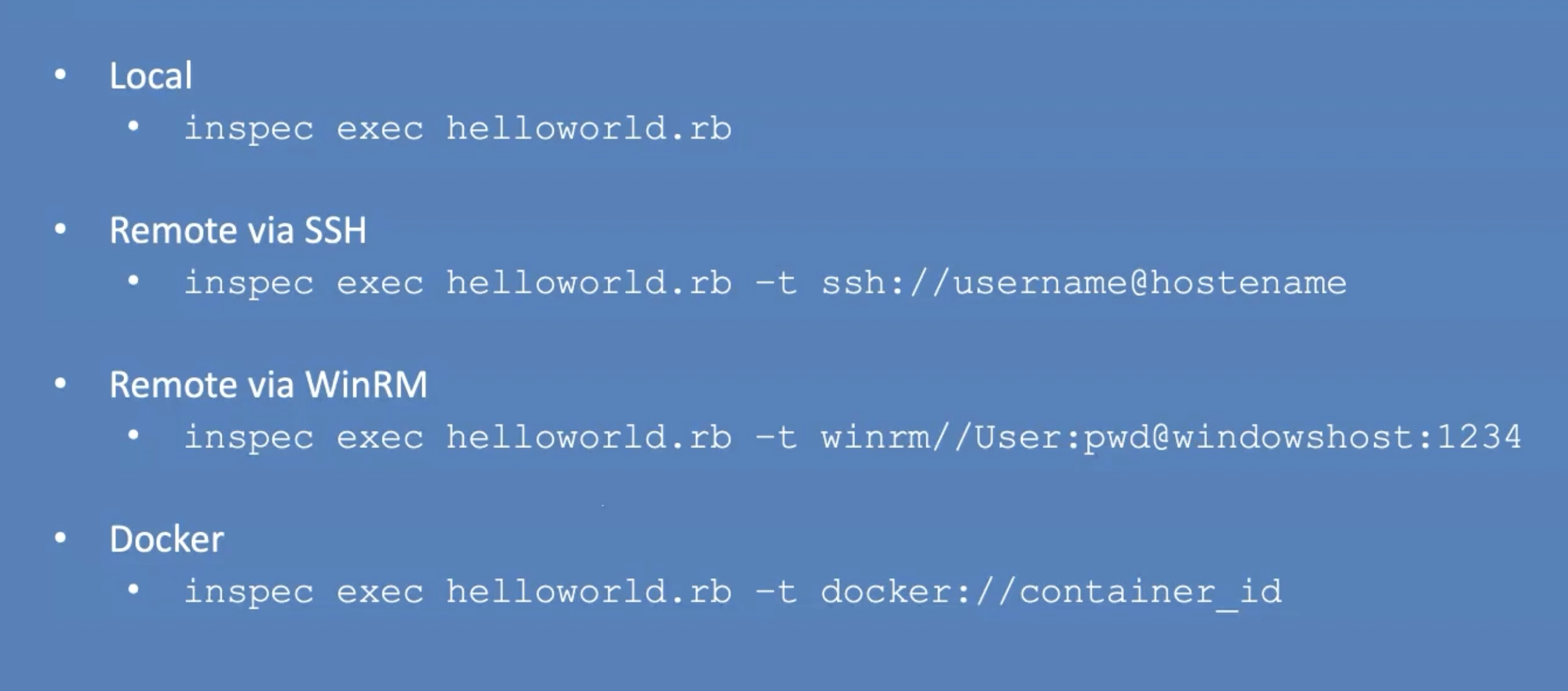
In the previous lesson, we have seen how the "Hello World" example was executed on the local machine.
# Execute a locally stored control or profile
Let's see how this works against a Docker container.
Go back to the terminal session.
First, I pull a Docker image within Tomcat with the following command.
docker pull tomcat
After the Docker images have a label, we can start the container with the following command.
docker run -d -it tomcat
Now you can verify the Docker container with the following command.
docker ps
Now, you'll see we have a local Tomcat in a Docker container running.
Now, we can execute our "Hello World" example against this container with the following command.
inspec exec helloworld.rb -t docker://0d643ba6ec94
With the -t option, we specify the target.
As the value for this target, we need a container ID.
Without a specified target, the control will be executed against the localhost.
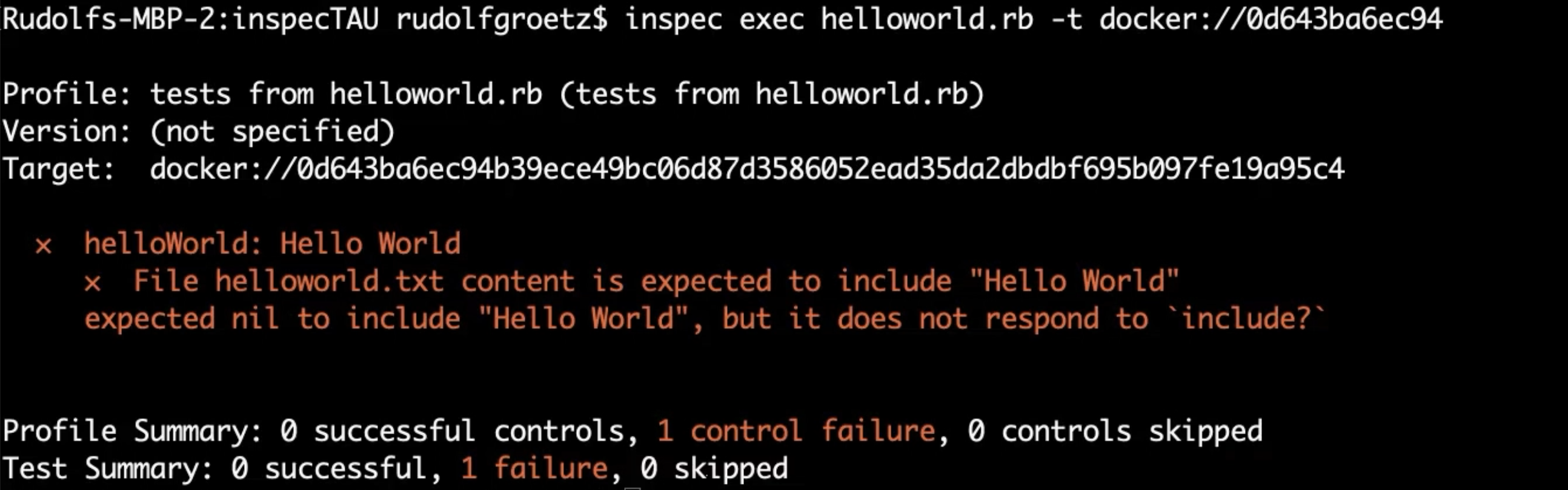
It is clear that this test failed since there is no helloworld.txt file in the Tomcat instance.
When we execute the Hello World example against the localhost, then we have a green test.

Until now, we only used controls which are stored locally on my machine.
# Execute a remotely stored control or profile
In this lesson, we are going to execute a control file or a profile that is stored in a remote repository.
In the World Wide Web, you will find many controls and profiles that you can use to scan your targets.
The DevSec project and the Center for Internet Security offer many profiles, as well as the Chef Supermarket.
You can download or clone these profiles or use it directly.
Let's get our hands dirty. Go back to the terminal session.
You can download or clone these profiles or use them directly.
Let's check out how it works.
First, we start a profile from the DevSec Project.
Details about this profile you can find at the official GitHub page.
We execute the Docker benchmark on our local machine with the following command.
inspec exec https://github.com/dev-sec/cis-docker-benchmark
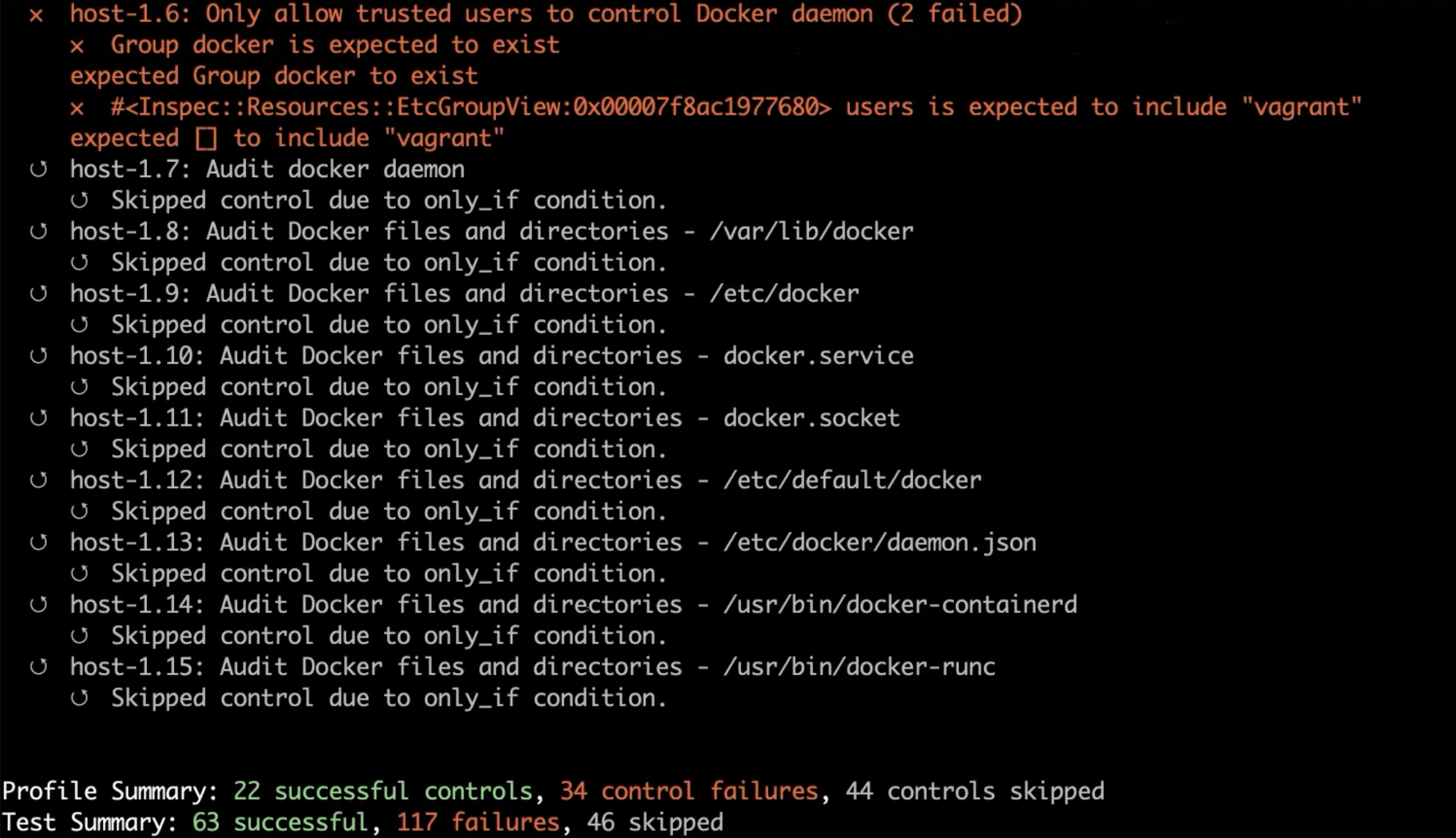
As you can see, our Docker installation is not in good shape, but anyway...
Now, we can look at how we run the profile from the Chef Supermarket.
First, you must know which profiles are available, an overview you can get with the following command.
inspec supermarket profiles
Now, we know which profiles are available in the Supermarket.
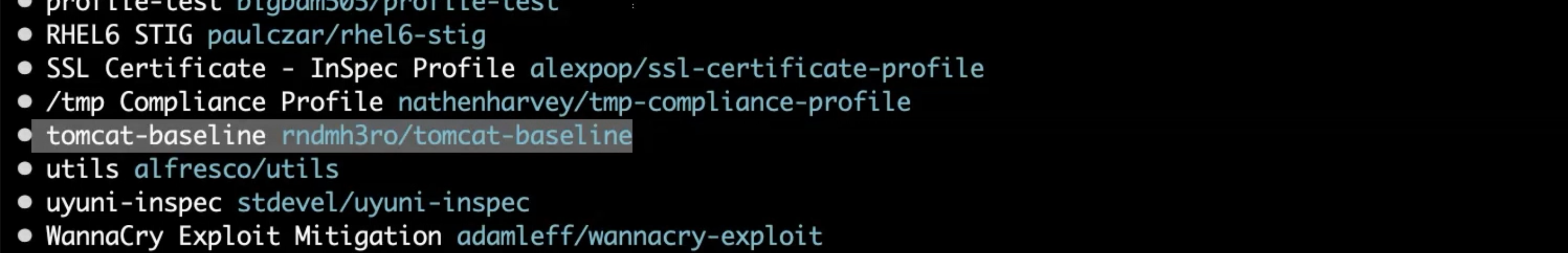
Let's use the tomcat-baseline and see if our local Tomcat is compliant.
You run the profile from the Chef Supermarket with the following command.
inspec exec supermarket://rndmh3ro/tomcat-baseline
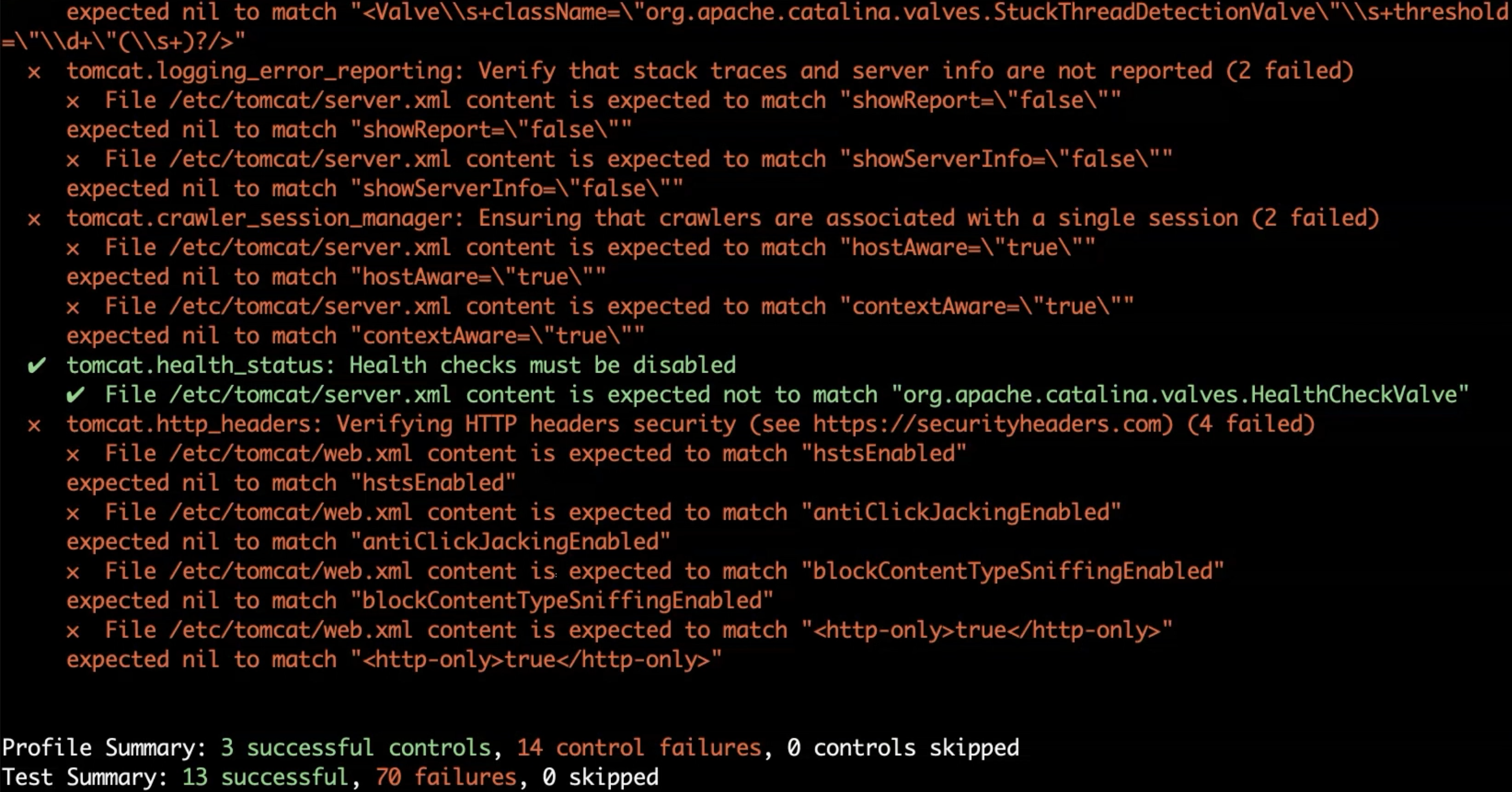
Our installation is not configured as it should be.
So, you have seen how you can execute remote profiles. That's all for the exec command.
# The shell command
Now, we'll jump to the shell command.
The next InSpec command which we contemplate is the shell command.
The shell command opens an interactive debugging session where you can examine controls and resources on your local workstation, a remote target or a cloud provider.
The shell makes it possible to use the Inspec DSL without creating any controls or profiles.
It is a typical REPL - REPL stands for Read-eval-print-loop, also known as Interactive Language Shell and is a simple interactive programming environment that takes single user inputs, executes them and returns the restart to the user - that's all - not more, not less.
How does it work?
Back to our terminal session.
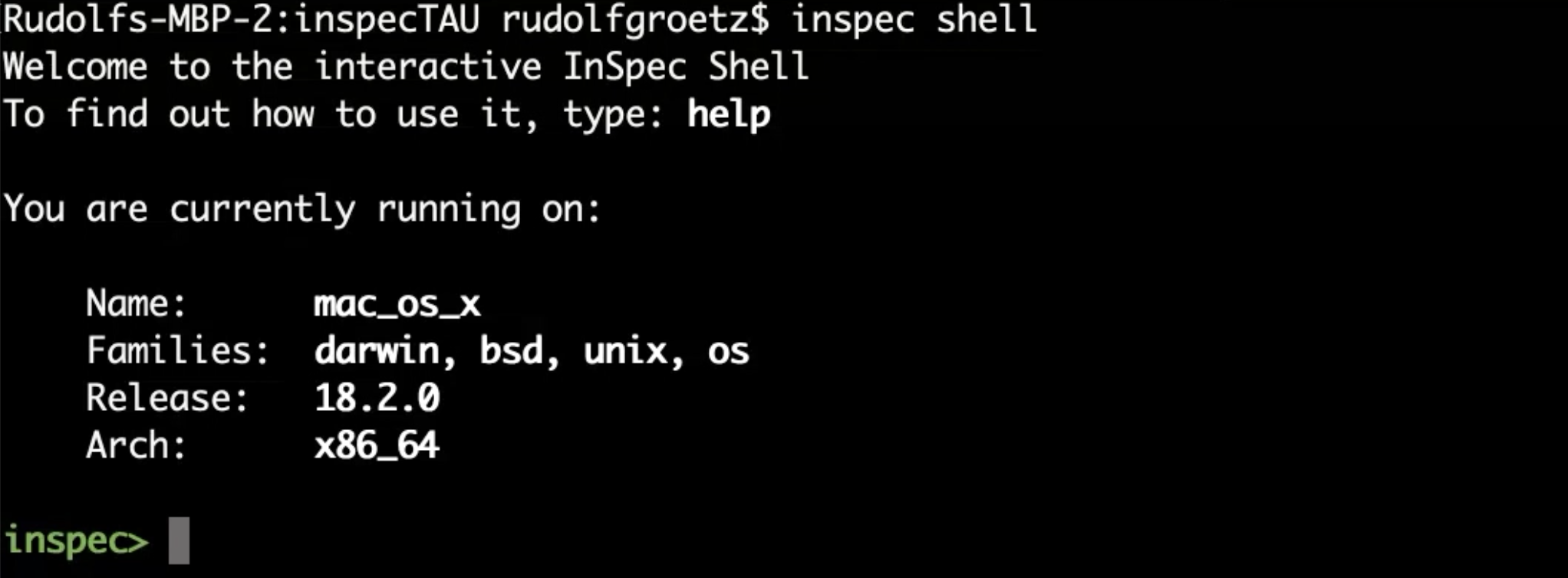
To launch an interactive InSpec session, run:
inspec shell
The shell welcomes you with details about your operating system.
To get an overview about the commands of the shell, the first command that we are using is help.
If you want to have more details about a given command, for example, the resource command, execute the following.
help resources
help resources gives you an overview about all resources that are available.
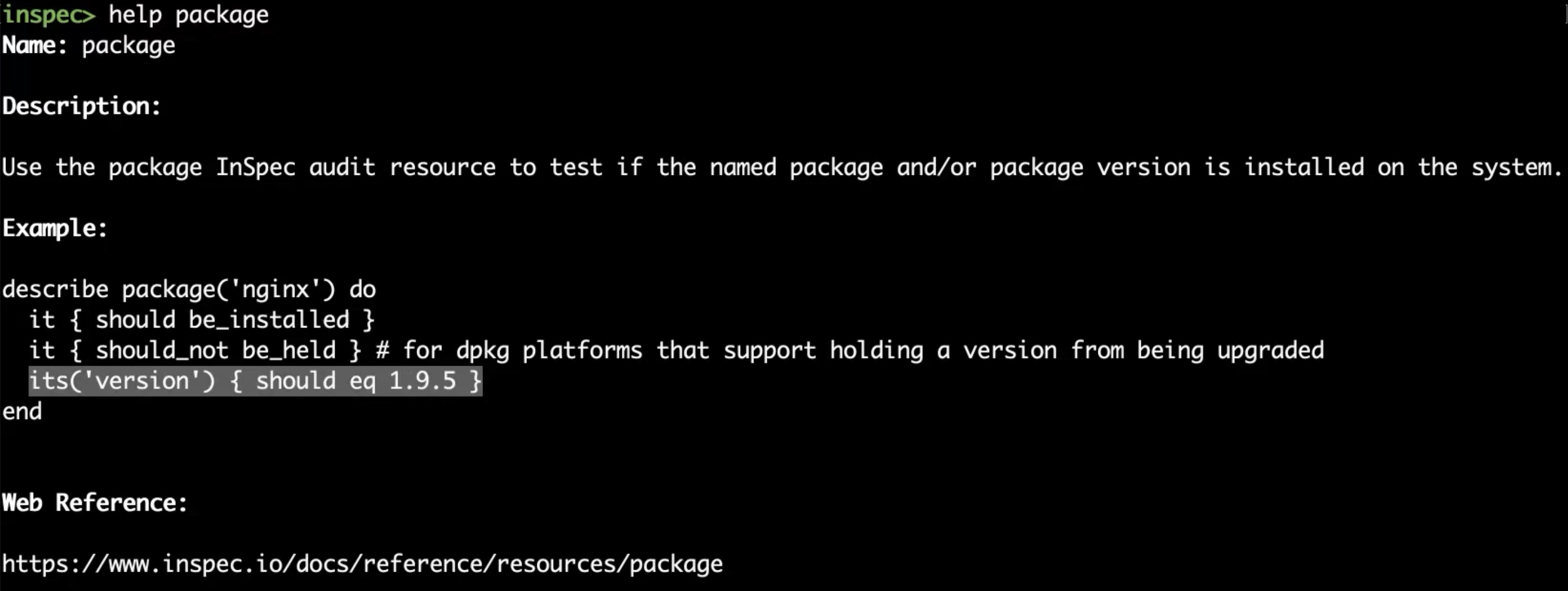
Let's use the package command to examine a given package on the system.
Run the following command to get an overview about the package resource.
help package
You'll see that you can test if a package is installed or what's the version of the package.
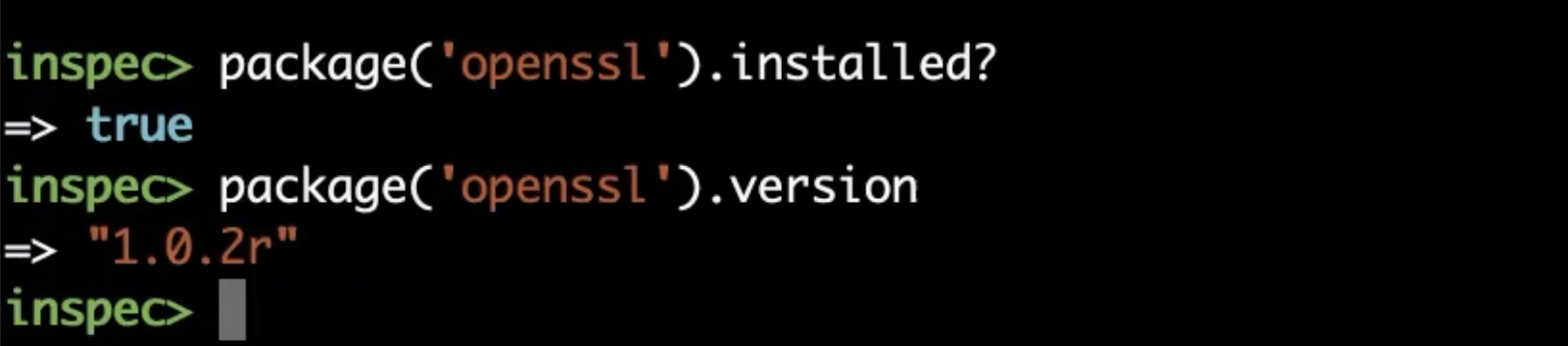
Let's see if the OpenSSL package is installed.
Do this with the following command.
package('openssl').installed?
You want to know which version of OpenSSL is installed?
package('openssl').version
So, we have enough to work with the shell as a REPL.
We are at the end of this chapter.
Now, you know the details about the exec command and the shell command.
