
Transcripted Summary
Hello again. In this chapter, we are going to understand what blockchain is.

Blockchain is the name of a whole new technology. It is a sequence of blocks or groups of transactions that are chained together and distributed among the users or nodes. It works as a record of transactions that do not require or rely on an external authority to validate the data.
# Blockchain Structure
Let's talk about the structure of a blockchain.
# Blockchain Structure — Hash
A hash is a cryptographic function that transforms any input data into a fixed length string of numbers.
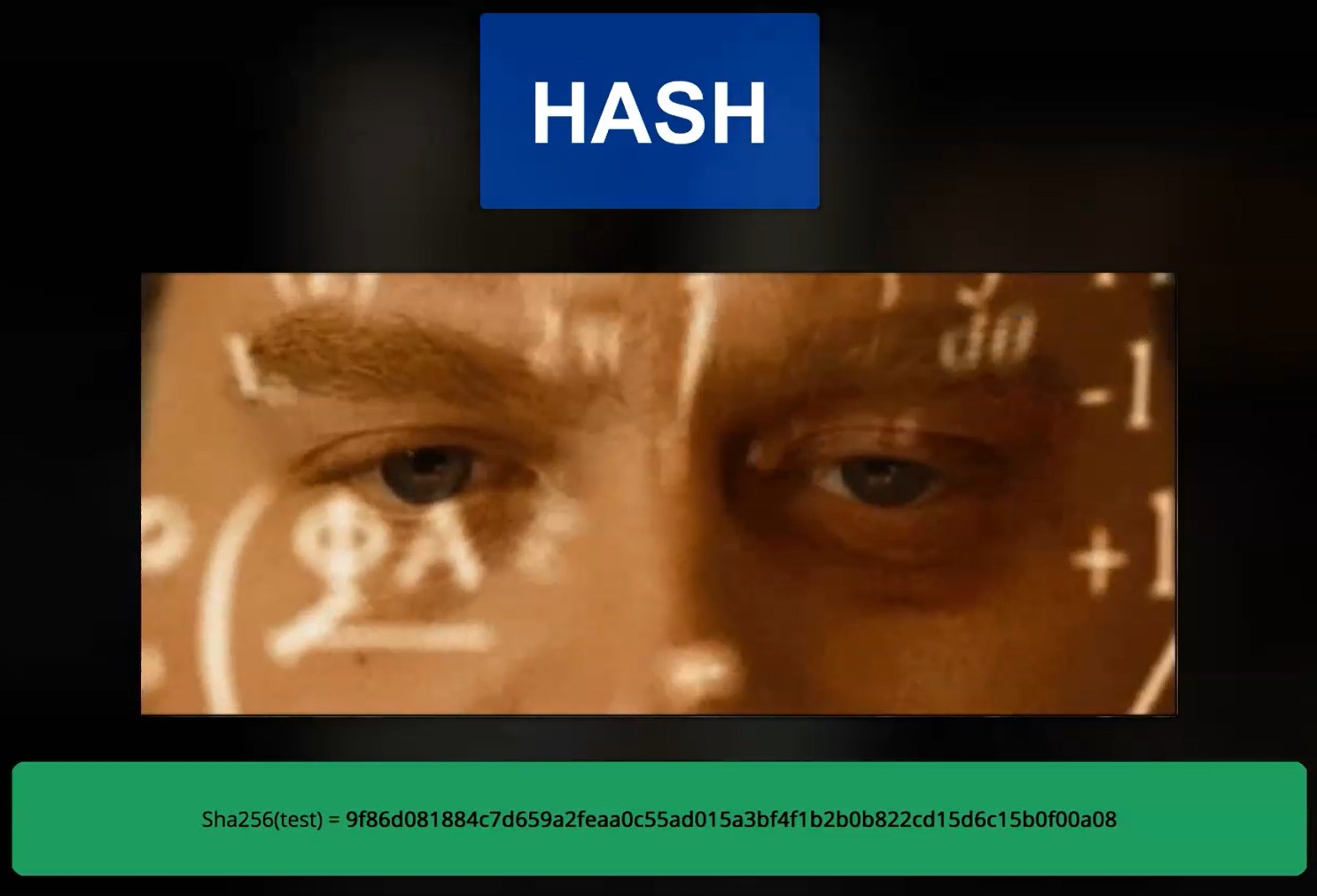
One of the most important features of the hash functions is that the conversion is one way. You cannot reverse the function to generate the original input.
# Blockchain Structure — Immutable Ledger
This feature is tightly related to the previous one. Since every block of the chain contains the hash of the previous one, it is not possible to modify any block without changing the entire chain.
Imagine if you are doing a Git commit. You just keep adding new commits, even if they have an error. You basically cannot revert.
If an anonymous attacker removes, adds, or modifies any transaction in this first block, the hash one (hash 1 - SHA-1) will change. As hash 1 (hash 1 - SHA-1) is included in block 2, hash two (hash 2 - SHA-2) that is generated from block 2 will change as well.
The error will propagate through every block of the chain, after the block under attack. The user will then declare the chain invalid.
# Blockchain Structure — Peer-to-Peer (P2P) Network
The blockchain doesn't need any external or internal trust authority. This is possible because the data is distributed among all the users. Every user has its own copy of the transactions and hashed blocks, and they spread the information to the entire network.
This way it is not possible for anyone to alter the information in the chain, since it is not started by a single entity, but for an entire network of users. Once a block of transactions is validated, it is added to the chain and every user updates their local information.
Even if an attacker were to modify your local chain, the network will not accept any block from the altered chain.
# Blockchain Structure — Consensus Protocol
What is consensus protocol? Users need to meet in agreement about the validity of the chain before adding more blocks. Every time a node adds a new block, all the nodes have to validate the block by using a common protocol.
Typically, the nodes reach a consensus about the correctness of a new block by proof of work (PoW) or proof of stake methods (PoS). The nodes check that the new block meets the requirements of their proof method. And if the block is valid, they consider it as part of the blockchain and keep adding new blocks.
# Blockchain Structure — Block Validation or 'Mining'
This feature is actually not really necessary for a blockchain. You can have no mining networks as well, like the crypto Ripple.
The term mining refers to the act of meeting the proof of work requirements for adding a new block with pending transactions to the blockchain. The proof of work method usually requires the user to create a block with restrictions on its hash code.
Since the hash code is unpredictable, the miners have to test any possible combination before meeting the requirements.
Once a miner node finds the solution to the proof of work problem, they add this block to the chain and every other node checks the validity according to their consensus protocol.
# Blockchain Principles

Now, we can talk about the principles of blockchain.
When most people talk about blockchain today, they mean a distributed database with a collection of blocks of data.
They often mean a database that's readable by many people, maybe everyone, but cannot be easily updated by a single user.
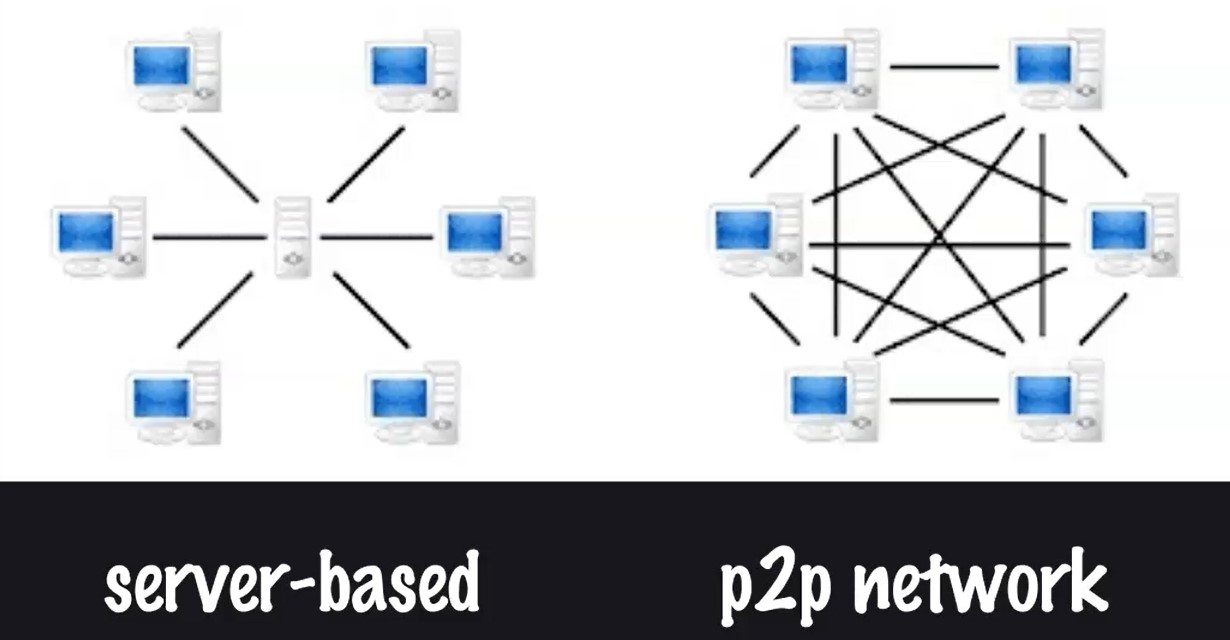
A peer-to-peer architecture instead of a client server architecture is also a key feature of a blockchain, which can let users carry out transactions without using a trusted third party.
There are six principles for blockchain development and implementation.
# Blockchain Principle #1 — Open
The blockchain solution should be open source, allowing anyone to contribute to its growth. The open-source tag will also bring innovation and ensure that quality code is maintained.
# Blockchain Principle #2 — Permissioned
Blockchains should be permissioned. Networks that are permissioned are designed to work in a closed ecosystem by keeping key features of blockchain intact. It promotes confidentiality and trust and ensures that illegal activities can be controlled.
Permissioned networks also ensure that only trusted entities can interact with the network, making it more secure and viable in the long run.
# Blockchain Principle #3 — Governance
Enterprise blockchain should have a proper governance system. It enables administrators to run and maintain the network.
A strong governance ensures that no one can abuse the network for their advantage. Admins can take the necessary steps to stop malicious actors before they start to attack the network or to stop them during the attack.
# Blockchain Principle #4 — Security
Security needs should be top notch for any blockchain development. Block chains are secure, but they still require proper security planning and execution. Also, it is an ongoing process, and it needs to have a periodic check to ensure plausible integrity.
# Blockchain Principle #5 — Standards
With **interoperability standards **it is easy for teams to work across different requirements, needs, or integrations.
# Blockchain Principle #6 — Privacy
Without the right to privacy, a blockchain solution cannot do justice to its other features such as transparency or immutability.
# Blockchain Fork
Now let's go to what forking means in the blockchain world.
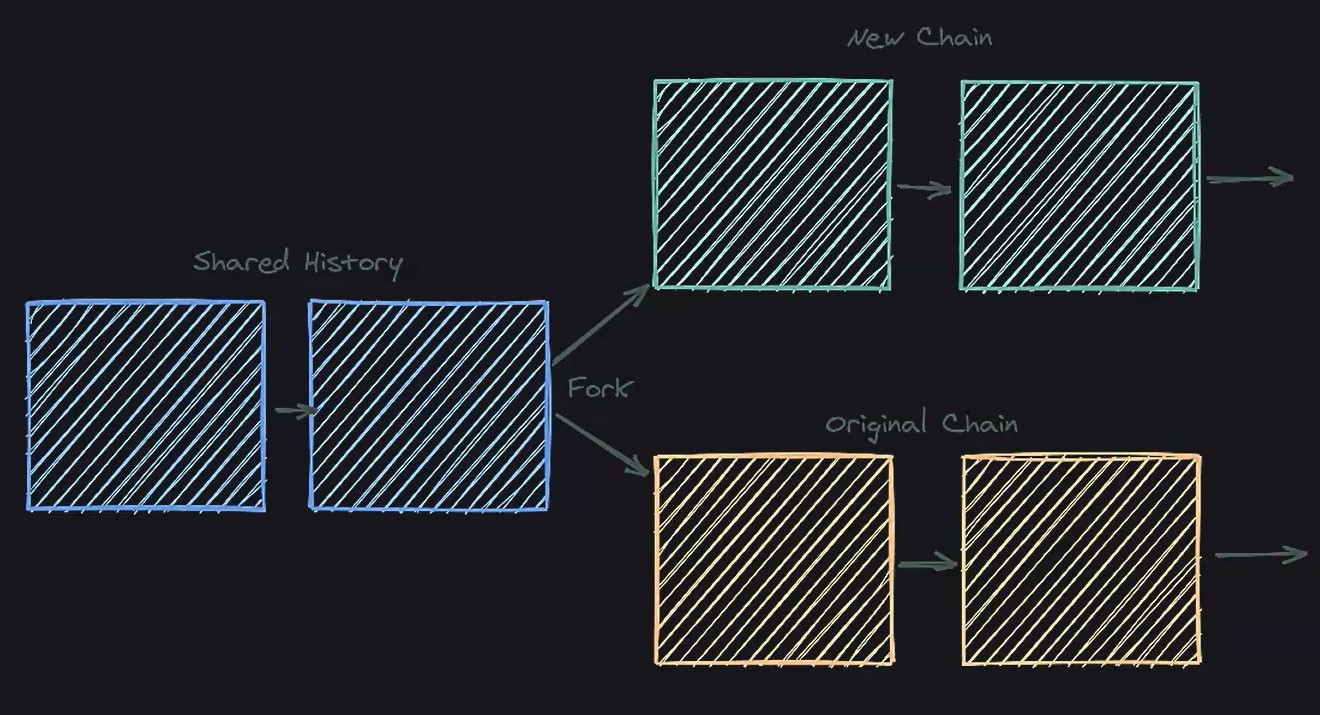
A fork is a split in the blockchain network. It happens when a blockchain diverges into 2 potential paths forward; or when there is a change in the protocol or when 2 or more miners find a block nearly at the same time.
Forks are related to the fact that different parties need to use common rules to maintain the history of the blockchain. And when parties are not in agreement, alternative chains can be created.
# Soft (Short Lived) Fork
You can have soft, short lived forks that are due each of the difficulty of reaching fast consensus in a distributed system.
# Hard (Permanent) Fork
And you can also have the hard permanent fork that can be used to add new features to a blockchain or reverse the effects of hacking.
# Future of Blockchain
Even though blockchain is often discussed in financial services and cryptocurrencies, this technology offers a broader range of potential applications. The blockchain technology is permanently evolving and provides a lightning fast, cheap alternative to establish cross border transactions for all business types.
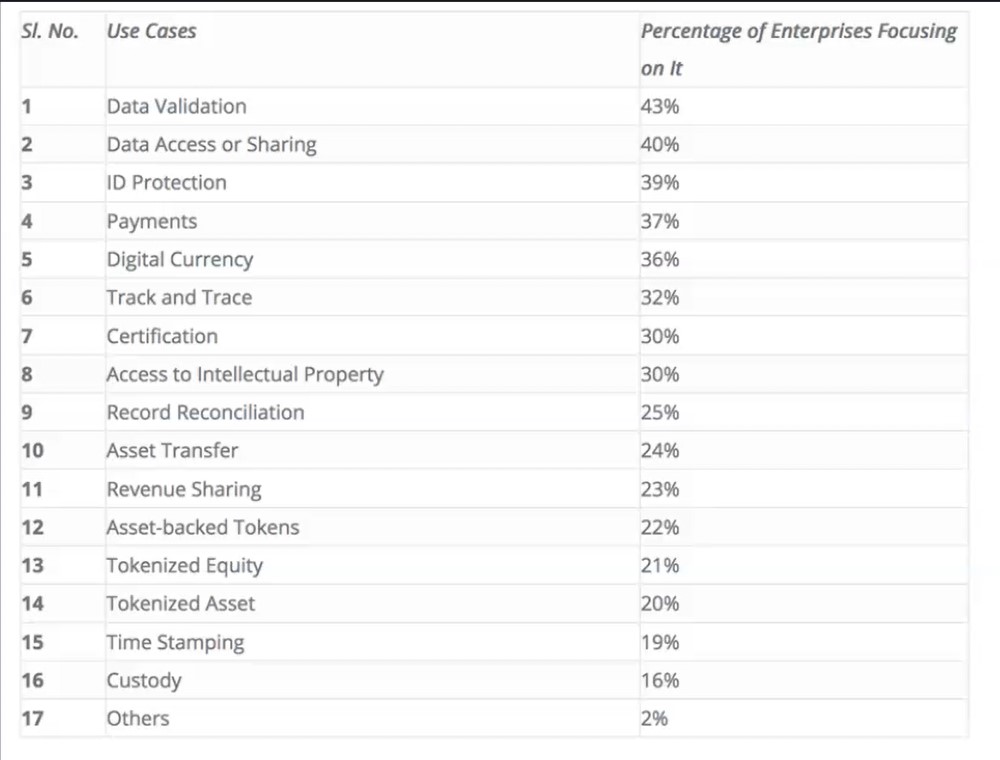
It is predicted that blockchain technology will be seen as the most important innovation to emerge from the cryptocurrency boom.
You can see some examples of blockchain use cases that companies are using nowadays in the picture above.
# Type of Tests for Blockchain
# API and Integration Testing
In API and integration testing, we ensure that the interaction between applications in the blockchain ecosystem is as expected.

# Block/Peer/Node Testing
All the blocks on the network should be tested individually to ensure proper cooperation. Here you check if the nodes in the network sync with other validating peers and if the integrity of the network and the shared ledger is maintained true to testing.
# Functional Testing
You also need to perform functional testing to evaluate the work of various functional parts of the blockchain like check user balance, transactional operations, et cetera.
# Performance Testing
Here, you check on the network latency based on its block size, network size, expected transaction size, and how long a query takes to return the search.
# Smart Contract Testing
Smart contract testing refers to validating transactions, meeting predefined conditions and business logic. Testing smart contracts involves simulation of all possible expected and unexpected variables for every contract and trigger that utilize the functions.
# Security Testing
Security testing is one of the most important parts. Here we ensure that the application is not vulnerable to attacks and the systems can protect that data.
# Attacks on the Blockchain
As blockchain grows, the attacks get very sophisticated and can cause huge damages.
# 51% Attack
One popular attack is the 51% attack.
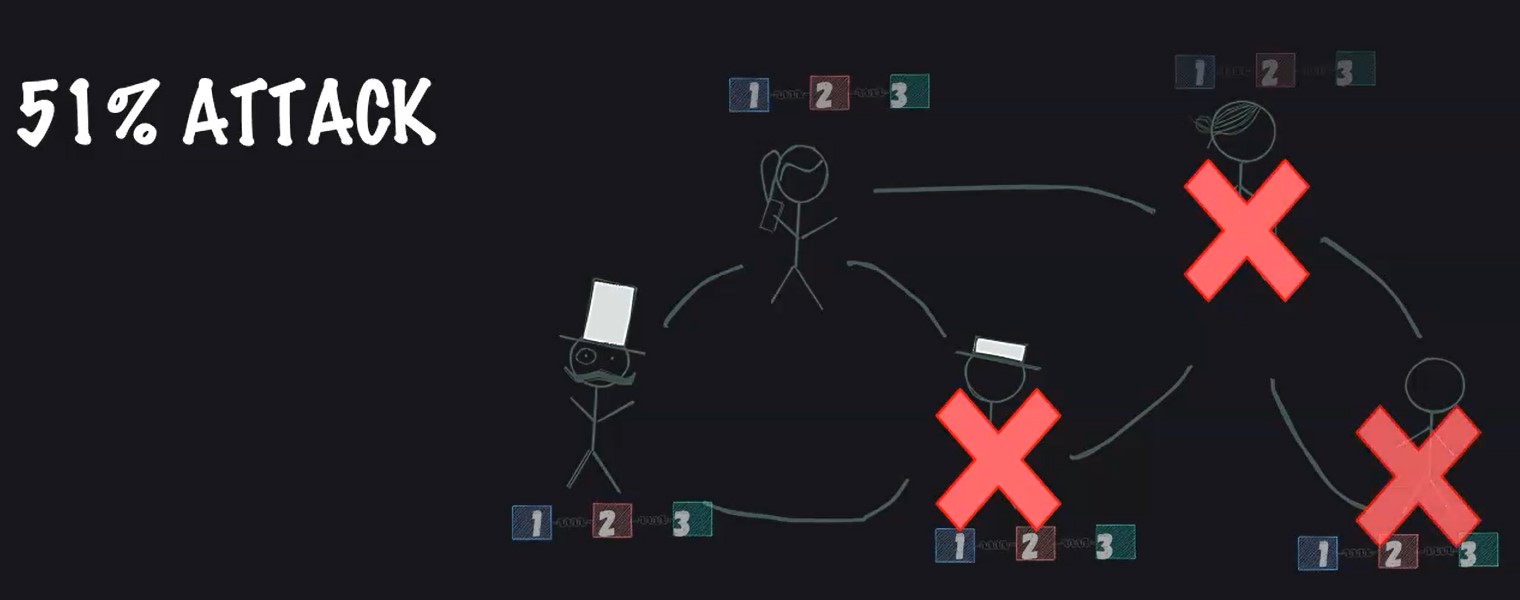
It is an attack on a blockchain by a group of miners who control more than 50% of the network. Attackers with majority control of the network can interrupt the recording of new blocks by preventing other miners from completing blocks.
# Mining Malware Attack
Malware uses the computing power of other computers to mine cryptocurrencies for hackers. China reported that over a million computers were infected by this malware and helped attackers mine more than 26 million tokens of various cryptocurrencies.
# DAO Attack
A famous attack that changed the history of the blockchain was the DAO Attack.
The DAO was essentially a decentralized sort of venture capital or hedge fund that was going to fund decentralized applications. Also called Dapps (short for decentralized applications), they were built on the Ethereum blockchain.
The DAO was attacked in June 2016 and the attacker was able to get $50 million.
The bug found can be also called the “Race-To-Empty” or a recursive call attack.
Let's dig a bit into the code.
# BankAttacker.sol Code
Here you have the BankAttacker contract containing the malicious code that interacts with the DAO contract.
contract BankAttacker {
bool is_attack;
address bankAddress;
function BankAttacker(address _bankAddress, bool _is_attack) {
bankAddress = _bankAddress;
is_attack = _is_attack;
}
function() {
if (is_attack == true) {
is_attack = false;
if (bankAddress.call(bytes4(sha3("withdrawBalance()")))) {
throw;
}
}
}
function deposit() {
if (
bankAddress.call.value(2).gas(20764)(
bytes4(sha3("addToBalance()"))
) == false
) {
throw;
}
}
function withdraw() {
if (bankAddress.call(bytes4(sha3("withdrawBalance()"))) == false) {
throw;
}
}
}
This fallback function from the attacker was the key point for this attack.
Ethereum uses a programming language called Solidity.
A Solidity contract can have one anonymous function known as well as the fallback function. This function doesn't take any arguments and is triggered on a call to the contract if none of the other functions match the given function signature, or if no data was supplied at all, and there is no Receive Ether Function.
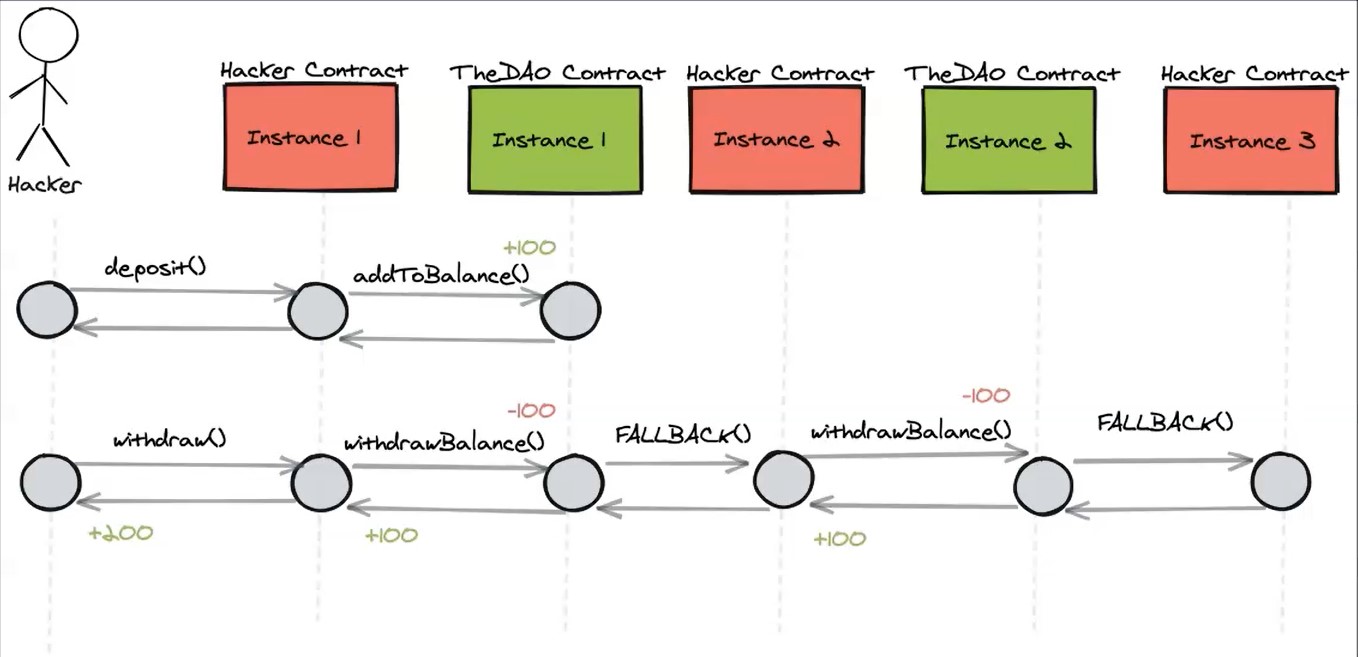
In the graphic above you see the attacker triggers the malicious contract from his account so this contract can interact with the vulnerable contract.
The Ethereum low level programming language executes instructions synchronously one after another. And this is why the user balance for variables is updated only after the previous code is finished.
The hacker sends Ether to the DAO contract through the deposit function deposit() of the hacker contract. Then this function calls the add to balance function addToBalance() of the DAO contract.
The hacker then withdraws through the DAO contract the same amount, triggering the withdraw balance function withdrawBalance() to the DAO contract.
The withdraw balance function sends Ether to the hacker contract, triggering its fallback function FALLBACK() and the last update the user balance variable.
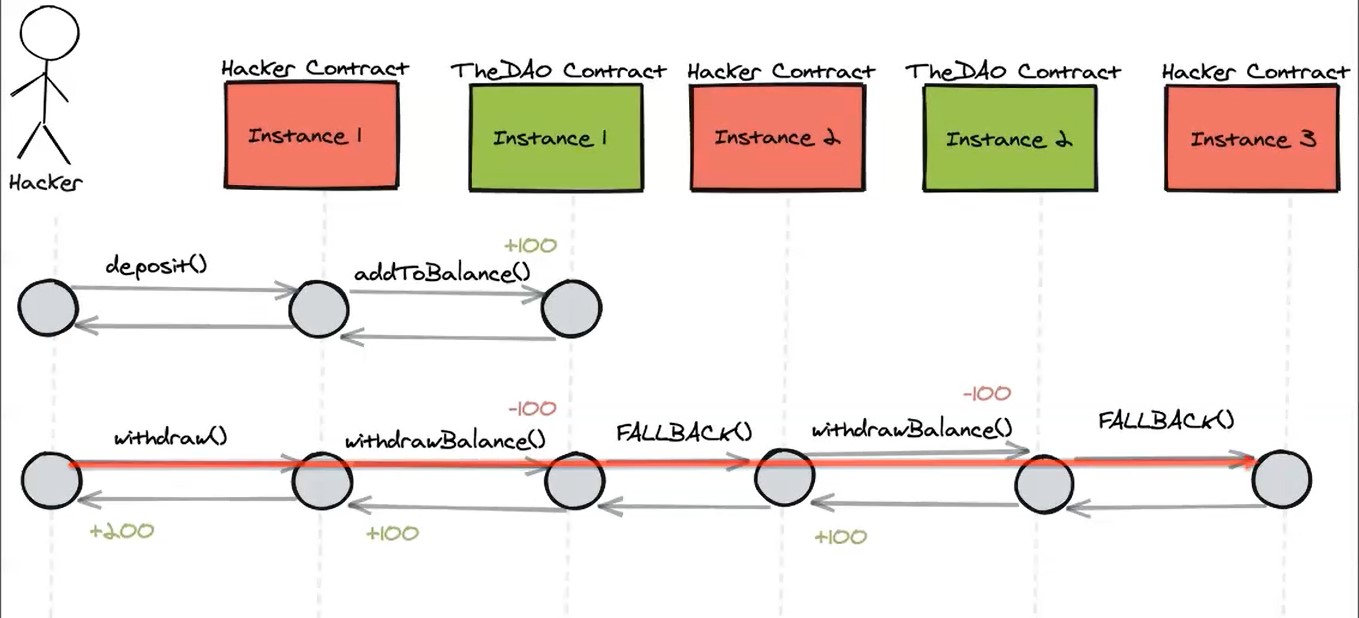
The malicious fallback function calls the withdraw balance function again, this recursive call, doubling the withdrawal before the first withdrawal balance function had finished, and without updating the user balances variable.
A test checking the balance of the account when a contract triggers the fallback function would have caught this bug.
What happened?
Well, the hack was reversed in the following weeks and the money was restored via hard fork of the Ethereum blockchain.
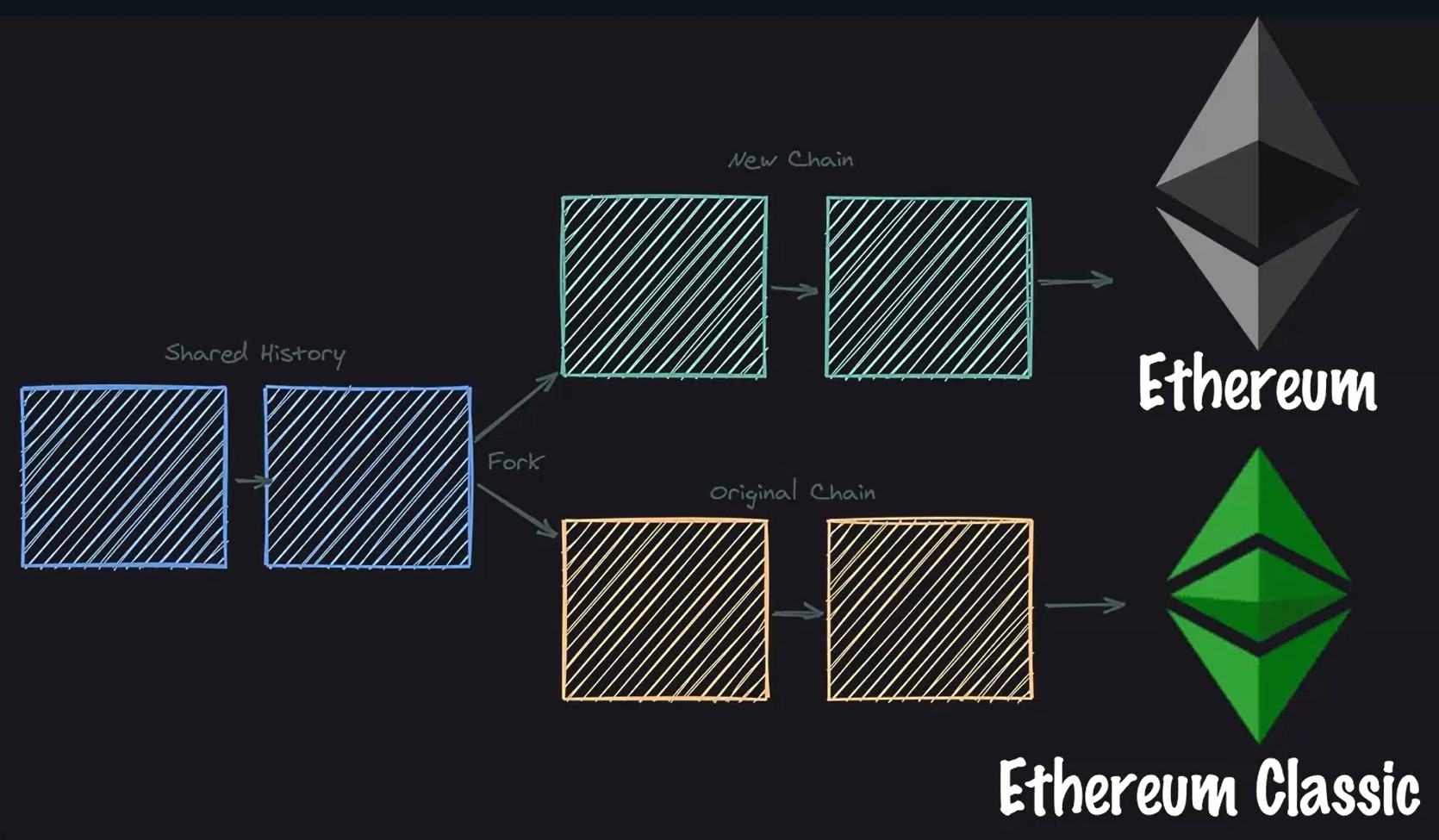
The Ethereum miners and the clients switched to the new fork, which continues to be called Ethereum.
And the original chain was called Ethereum Classic and is used by ideologists that were unshaken in their beliefs of immutable ledger.
Ethereum was first created as an instance against financial corruption. The multiple blockchain was meant to be free from the human tendency to corrupt.
The DAO hack, which had nothing to do with the integrity of the Ethereum blockchain, divided the Ethereum community because of the decision to hard fork, which was essentially manipulating the blockchain, and it went against the principles of the blockchain.
# Blockchain Testing Tools
Ethereum Tester is an open-source testing library available as a GitHub repo. The setup is pretty easy in Python with manageable API support for various testing requirements.
BitcoinJ is a Java based framework built for Bitcoin based apps and enables you to interact with the real BTC network.
Brownie is a Python based development and testing framework for smart contracts targeting the Ethereum virtual machine. It’s developed around the Python framework, and it's quite easy to implement.
Truffle, often used by Ethereum developers, brings in good testing features such as automated contract testing.
Embark is an Ethereum testing framework that focuses on developing decentralized applications and runs on various systems or nodes.
In the next chapter we are going to set up our own lockout blockchain. See you there.
